You are using an out of date browser. It may not display this or other websites correctly.
You should upgrade or use an alternative browser.
You should upgrade or use an alternative browser.
GamersOnLinux
Dark Fracture in PlayOnLinux
Sep 09
- 2,987
- 0
Dark Fracture is a first person psychological horror/puzzle game. You work at a morgue and have to stay late one night, but are you alone? Strange sounds come from dark rooms and bloodstains suddenly appear on the floor... the electricity goes out... find your lighter and get out!

https://twisted2studio.itch.io/dark-fracture
ProtonGE 5.0 was able to handle this demo just fine in PlayOnLinux as it was developed in Unreal Engine. I didn't have any performance issues or graphical issues... the demo ran perfectly on my GeForce GTX 1060 with DXVK 1.7
Specs:
Mint 19.3 64-bit
GeForce GTX 1060
Nvidia 440.100
ProtonGE 5.0 64-bit
DXVK 1.7 64-bit
Note: Also requires vcrun2019 and Media Foundation installation






 ...
...
https://twisted2studio.itch.io/dark-fracture
ProtonGE 5.0 was able to handle this demo just fine in PlayOnLinux as it was developed in Unreal Engine. I didn't have any performance issues or graphical issues... the demo ran perfectly on my GeForce GTX 1060 with DXVK 1.7
Specs:
Mint 19.3 64-bit
GeForce GTX 1060
Nvidia 440.100
ProtonGE 5.0 64-bit
DXVK 1.7 64-bit
Note: Also requires vcrun2019 and Media Foundation installation
Mirror's Edge in Proton
Sep 07
- 4,427
- 0
Back in 2013 I posted a step-by-step guide on how to install Steam in PlayOnLinux and run Mirror's Edge. It was a lot of worked to get it setup. But today you can seriously just run it in Proton through Linux Steam.

Game Play
Mirror's Edge runs great in Proton as it is a DirectX 9 game. I was able to crank all the settings to high and play without any bugs or crashes. The game saved and continued without issues either. This is great for us gamers because Proton handles everything from DirectX & Visual C+ installation to Physx setup.
Specs:
Mint 19.3 64-bit
GeForce GTX 1060
Nvidia 440.100
Proton 5.0-9







 ...
...
Game Play
Mirror's Edge runs great in Proton as it is a DirectX 9 game. I was able to crank all the settings to high and play without any bugs or crashes. The game saved and continued without issues either. This is great for us gamers because Proton handles everything from DirectX & Visual C+ installation to Physx setup.
Specs:
Mint 19.3 64-bit
GeForce GTX 1060
Nvidia 440.100
Proton 5.0-9
Yarntown in PlayOnLinux
Sep 03
- 3,506
- 0
Yarntown is a zelda-like action RPG in a mysterious Gothic town full of bandits and creatures. Inspired by Bloodborne, your character can wield several weapons and self-heal. Find hearts and survive the maze-like town with destructible objects and puzzles.

https://maxatrillionator.itch.io/yarntown
https://gitlab.com/maxmraz/yarntown
I was unable to install the Solarus engine and play the native Linux version of Yarntown, so I just used PlayOnLinux and ran the windows version with Wine. The game ran beautifully and it is cleverly crafted. They are doing an amazing job with 2D elements in a 3D-ish world. Use your roll/dodge ability to avoid taking hits and then shoot them down or slay em with your sword. Unfortunately if you die, all the enemies respawn and you begin at the last lantern save point.
Specs:
Mint 19.3 64-bit
GeForce GTX 1060
Nvidia 440.100
PlayOnLinux 4.3.4
Wine 5.0 64-bit
 ...
...
https://maxatrillionator.itch.io/yarntown
https://gitlab.com/maxmraz/yarntown
I was unable to install the Solarus engine and play the native Linux version of Yarntown, so I just used PlayOnLinux and ran the windows version with Wine. The game ran beautifully and it is cleverly crafted. They are doing an amazing job with 2D elements in a 3D-ish world. Use your roll/dodge ability to avoid taking hits and then shoot them down or slay em with your sword. Unfortunately if you die, all the enemies respawn and you begin at the last lantern save point.
Specs:
Mint 19.3 64-bit
GeForce GTX 1060
Nvidia 440.100
PlayOnLinux 4.3.4
Wine 5.0 64-bit
Dungeon Nightmares II in PlayOnLinux
Sep 02
- 2,900
- 0
Dungeon Nightmares was so good that I stumbled on the sequel and decided to purchase it!
Dungeon Nightmares II is a much improved horror experience with a new story-like experience. You wake up in a mysterious hotel room with the time of day on the screen. Exploring the hallways is useless as none of the doors are unlocked... but at the end of a hallway is a creepy elevator. Take it down to the basement dungeon and find a way out. Alive if at all possible!

All the same features from the origin Dungeon Nightmares are here:
Dungeon Nightmares II is a much improved horror experience with a new story-like experience. You wake up in a mysterious hotel room with the time of day on the screen. Exploring the hallways is useless as none of the doors are unlocked... but at the end of a hallway is a creepy elevator. Take it down to the basement dungeon and find a way out. Alive if at all possible!
All the same features from the origin Dungeon Nightmares are here:
- Jump Scares
- Spooky Environment
- Exploration
- Roguelike
- Procedural Generation
- Small Download
- Replayability
Disaster Report 4 Demo in PlayOnLinux
Aug 28
- 2,564
- 0
Disaster Report 4 is like a natural disaster simulation. Create your character, personality and then within minutes you are thrust into an earthquake right in the middle of a busy downtown in Japan. Decide if you will help people or help yourself. Explore a broken city with immediate danger around every corner.

https://www.gog.com/game/disaster_report_4_summer_memories_demo
Disaster Report was built in Unreal Engine and ran very well with ProtonGE on my GeForce GTX 1060. At first the game wouldn't run at all, probably because my wineprefix was missing DXVK. Once that was all setup, the game launched and played perfectly! I had never heard of Disaster Report before and wasn't sure what it was about... after playing the demo, I'm anxious to see what happens next.
Specs:
Mint 19.3 64-bit
GeForce GTX 1060
Nvidia 440.100
ProtonGE 5.0-9 64-bit
DXVK 1.7 64-bit
 ...
...
https://www.gog.com/game/disaster_report_4_summer_memories_demo
Disaster Report was built in Unreal Engine and ran very well with ProtonGE on my GeForce GTX 1060. At first the game wouldn't run at all, probably because my wineprefix was missing DXVK. Once that was all setup, the game launched and played perfectly! I had never heard of Disaster Report before and wasn't sure what it was about... after playing the demo, I'm anxious to see what happens next.
Specs:
Mint 19.3 64-bit
GeForce GTX 1060
Nvidia 440.100
ProtonGE 5.0-9 64-bit
DXVK 1.7 64-bit
Them And Us in Proton
Aug 24
- 2,621
- 0
Them and Us is a 3rd person action horror adventure made in Unreal Engine. Play as Alicia waking up in a mysterious room in a huge mansion. As she searches for clues and tools she quickly discovers she is not alone. Explore the mansion and find weapons and tools to survive. What happened to the people who lived here? Can she find her way out alive?

Steam
https://store.steampowered.com/app/915600/Them_and_Us/
Itch.io
https://tendogames.itch.io/them-and-us
I stumbled on Them and Us searching for horror games on itch.io
I was unable to extract the download, but found the demo was also available on Steam. I was able to download and play the whole demo with Proton in Steam.
This is an amazing Resident-Evilesque-Inspired action game! In fact you can choose to have static camera views just like the original Resident Evil games, or use over-the-shoulder views. The game is fairly slow but intense at the same time. Progress is...
Steam
https://store.steampowered.com/app/915600/Them_and_Us/
Itch.io
https://tendogames.itch.io/them-and-us
I stumbled on Them and Us searching for horror games on itch.io
I was unable to extract the download, but found the demo was also available on Steam. I was able to download and play the whole demo with Proton in Steam.
This is an amazing Resident-Evilesque-Inspired action game! In fact you can choose to have static camera views just like the original Resident Evil games, or use over-the-shoulder views. The game is fairly slow but intense at the same time. Progress is...
Windows Universal Platform
Aug 21
- 3,010
- 0
Danger! Danger! Microsoft is doing it again...
Have you heard of Universal Windows Platform?
It appears Microsoft is trying to create an API to develop apps that work on all Microsoft platforms:
Is Microsoft going follow Apple and eventually kill all x86 compatible applications as well?
Since WUP supports C++, C#, F#, JavaScript, and VB.NET to develop apps I'm going to imaging x86 compatibility is still supported for the unforeseeable future. But what happens when they decide to go full Windows-As-A-Service platform or only support ARM processes for their games?
https://www.spec-india.com/tech-in-200-words/what-is-universal-windows-platform
Have you heard of Universal Windows Platform?
It appears Microsoft is trying to create an API to develop apps that work on all Microsoft platforms:
- PCs
- Smartphones
- Tablets
- Game consoles
- HoloLens
- IoT devices
Is Microsoft going follow Apple and eventually kill all x86 compatible applications as well?
Since WUP supports C++, C#, F#, JavaScript, and VB.NET to develop apps I'm going to imaging x86 compatibility is still supported for the unforeseeable future. But what happens when they decide to go full Windows-As-A-Service platform or only support ARM processes for their games?
https://www.spec-india.com/tech-in-200-words/what-is-universal-windows-platform
Eden in PlayOnLinux
Aug 20
- 2,808
- 0
Eden is a game developed by six graduate students in Unity 3D engine. In this surreal FP adventure you will find many unexpected turns and twists. This is no ordinary puzzle game, your mind will be tested and your patience stretched thin. Is there a way out?

https://missingmountain.itch.io/eden
Graphically Eden is cleverly designed with stylistic and beautiful textures. The models and assets are designed to enhance the environment without standing out. What you see is not what you think it is... Take a second look. I was truly amazed at the genius puzzles! I played through twice just to make sure I did everything.
Wine in PlayOnLinux was able to handle this game nicely on my GeForce GTX 1060. In fact I had to stop mid game and found that it saved my progress and I was able to continue. Eden is now one of my most favorite indie thrillers. I hope these developers make more games!
Specs:
Mint 19.3 64-bit
GeForce GTX 1060
Nvidia...
https://missingmountain.itch.io/eden
Graphically Eden is cleverly designed with stylistic and beautiful textures. The models and assets are designed to enhance the environment without standing out. What you see is not what you think it is... Take a second look. I was truly amazed at the genius puzzles! I played through twice just to make sure I did everything.
Wine in PlayOnLinux was able to handle this game nicely on my GeForce GTX 1060. In fact I had to stop mid game and found that it saved my progress and I was able to continue. Eden is now one of my most favorite indie thrillers. I hope these developers make more games!
Specs:
Mint 19.3 64-bit
GeForce GTX 1060
Nvidia...
Hellblade: Senua's Sacrifice in PlayOnLinux
Aug 18
- 2,685
- 0
Hellblade is a 3rd person psychological action adventure. Senua is trying to fight her inner-demons as she searching for her husband. You will fight in melee combat against all kinds of evil spirits as your inner voices help you solve the clever puzzles. Some would say this is a story game, but you only hear stories when interacting with a specific object in the game. Otherwise you are searching for puzzles and slaying minions.

https://www.gog.com/game/hellblade_senuas_sacrifice_pack
A few months back I saw Hellblade in a GOG sale. Checked ProtonDB to see if it ran well in Proton. Reports were looking good. So I purchased it and gave it a try... Stable Wine 5.0 64-bit ran it well with DXVK 1.7
Specs:
Mint 19.3 64-bit
GeForce GTX 1060
Nvidia 440.100
Wine 5.0 64-bit
DXVK 1.7 64-bit




 ...
...
https://www.gog.com/game/hellblade_senuas_sacrifice_pack
A few months back I saw Hellblade in a GOG sale. Checked ProtonDB to see if it ran well in Proton. Reports were looking good. So I purchased it and gave it a try... Stable Wine 5.0 64-bit ran it well with DXVK 1.7
Specs:
Mint 19.3 64-bit
GeForce GTX 1060
Nvidia 440.100
Wine 5.0 64-bit
DXVK 1.7 64-bit
Montti Constanttini in PlayOnLinux
Aug 17
- 2,441
- 0
Montti Constanttini is a first person horror puzzle game where you play as Jack, a little boy, who is can explore his dark spooky house. Find your stuffed animals and pack them away before you run out of time.
One of the most interesting features in Montti Constanttini is that Jack can look very closely at any object in the game. The perspective of the camera and Jacks smaller size give you more flexibility to look over the edge of tables or down into a box.
https://warvision.itch.io/montti-constanttini
Montti Constanttini was built in Unreal Engine, so you will need to use Proton GE and DXVK for it to run properly. My GeForce GTX 1060 was able to handle the game perfectly in PlayOnLinux.
Specs:
Mint 19.3 64-bit
GeForce GTX 1060
Nvidia 440.100
PlayOnLInux 4.3.4
Proton GE 5.9
DXVK 1.7 64-bit





 ...
...
One of the most interesting features in Montti Constanttini is that Jack can look very closely at any object in the game. The perspective of the camera and Jacks smaller size give you more flexibility to look over the edge of tables or down into a box.
https://warvision.itch.io/montti-constanttini
Montti Constanttini was built in Unreal Engine, so you will need to use Proton GE and DXVK for it to run properly. My GeForce GTX 1060 was able to handle the game perfectly in PlayOnLinux.
Specs:
Mint 19.3 64-bit
GeForce GTX 1060
Nvidia 440.100
PlayOnLInux 4.3.4
Proton GE 5.9
DXVK 1.7 64-bit
Virus Z Demo in PlayOnLinux
Aug 14
- 2,562
- 0
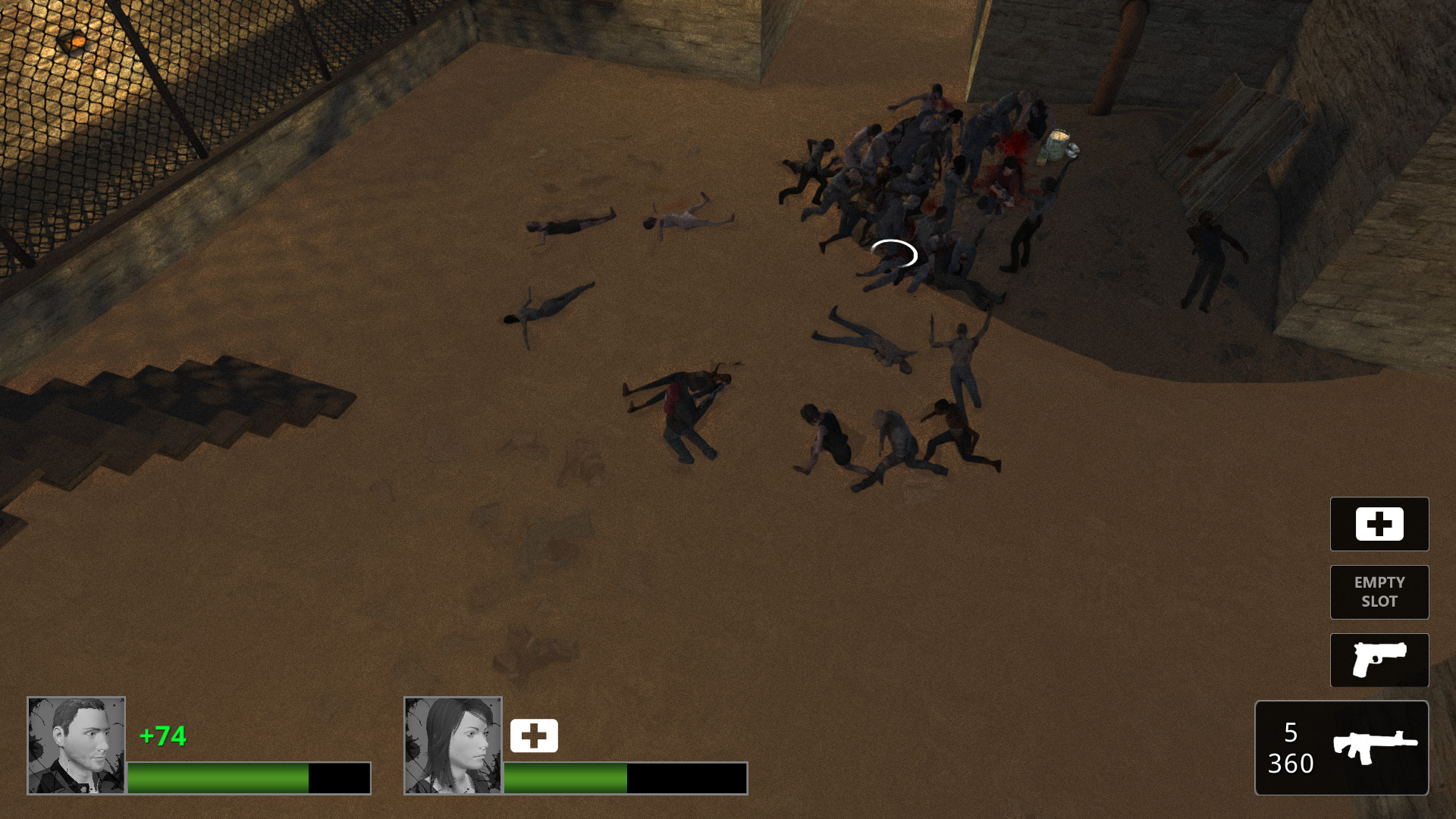
Virus Z is a top-down zombie shooter much like Left4Dead. You start on top of a building with your NCP companion. Pick a weapon on the table and some health, then start working your way through the city slaying zombies, hordes and mini bosses.
The demo includes a few linear maps and locations for you to traverse. If you survive and make it to the safe zone on the other side of the map, then you can continue to the next map.
https://seaalight.itch.io/virus-z
I was able to launch and play Zombie Z without any serious issues. Wine 5.0 64-bit & DXVK handle the Unity 3D game well on my GeForce GTX 1060 in PlayOnLinux.
Specs:
Mint 19.3 64-bit
GeForce GTX 1060
Nvidia 440.100
PlayOnLinux 4.3.4
Wine 5.0 64-bit
DXVK 1.7 64-bit





 ...
...
The demo includes a few linear maps and locations for you to traverse. If you survive and make it to the safe zone on the other side of the map, then you can continue to the next map.
https://seaalight.itch.io/virus-z
I was able to launch and play Zombie Z without any serious issues. Wine 5.0 64-bit & DXVK handle the Unity 3D game well on my GeForce GTX 1060 in PlayOnLinux.
Specs:
Mint 19.3 64-bit
GeForce GTX 1060
Nvidia 440.100
PlayOnLinux 4.3.4
Wine 5.0 64-bit
DXVK 1.7 64-bit
Notes Of Obsession in PlayOnLinux
Aug 10
- 3,979
- 0
Notes Of Obsession is a short First Person horror experience. Explore an empty house and work your way into a child's room to find a music box. When you play the music box secret symbols will appear and the nightmare begins.

How do you escape?
What is following you around the house?
https://creaky-stairs.itch.io/notes-of-obsession
Specs:
Mint 19.3 64-bit
GeForce GTX 1060
Nvidia 440.100
PlayOnLinux 4.3.4
ProtonGE 5.9
DXVK 1.7









How do you escape?
What is following you around the house?
https://creaky-stairs.itch.io/notes-of-obsession
Specs:
Mint 19.3 64-bit
GeForce GTX 1060
Nvidia 440.100
PlayOnLinux 4.3.4
ProtonGE 5.9
DXVK 1.7
Fallout 4 in Proton
Aug 08
- 5,425
- 0
I tested Fallout 4 a few years ago and found that there were some serious mouse and audio issues. Tried a bunch of workarounds and gave up. Test again later and same problems. Even the older Fallout games had some problems but could be resolved with a few hacks and overrides.
Today Fallout 4 runs great in Proton because of the DXVK efforts and faudio compatibility. I was able to run Fallout 4 with the following "launch options":
Fallout 4 plays almost perfectly on my GeForce GX 1060 with everything set to Ultra! There area few graphical bugs with loading textures/decals, but its rarely noticeable.
Specs:
Mint 19.3 64-bit
GeForce GTX 1060
Nvidia 440.100
Proton 5.0-9






 ...
...
Today Fallout 4 runs great in Proton because of the DXVK efforts and faudio compatibility. I was able to run Fallout 4 with the following "launch options":
Code:
WINEDLLOVERRIDES="xaudio2_7=n,b" PULSE_LATENCY_MSEC=90 %command%Fallout 4 plays almost perfectly on my GeForce GX 1060 with everything set to Ultra! There area few graphical bugs with loading textures/decals, but its rarely noticeable.
Specs:
Mint 19.3 64-bit
GeForce GTX 1060
Nvidia 440.100
Proton 5.0-9
Vouivre Prototype in PlayOnLinux
Aug 06
- 2,446
- 0
Vouivre is an interesting FPS where you explore a short dungeon and discover an ancient civilization possessed by aliens. Very similar to headcrabs, the alien will attach its-self to the hosts head and control them. Explore hallways of temple-like dungeon and find that you are not alone. After brutally slaying a host with your knife you realize it won't be enough to survive. Find a weapon and stay alive!
Vouivre ran well in ProtonGE with PlayOnLinux. I was able to play through the short demo without any crashes or graphical artifacts. This demo is very polished and professional. Voice acting is top notch as well as visuals. Animation and sound effects are engaging and professionally done. Too bad this was a student project as it would make an amazing full game!
https://teamvouivre.itch.io/vouivre
Specs:
Mint 19.3 64-bit
GeForce GTX 1060
Nvidia 440.100
ProtonGE 5.9
DXVK 1.7
 ...
...
Vouivre ran well in ProtonGE with PlayOnLinux. I was able to play through the short demo without any crashes or graphical artifacts. This demo is very polished and professional. Voice acting is top notch as well as visuals. Animation and sound effects are engaging and professionally done. Too bad this was a student project as it would make an amazing full game!
https://teamvouivre.itch.io/vouivre
Specs:
Mint 19.3 64-bit
GeForce GTX 1060
Nvidia 440.100
ProtonGE 5.9
DXVK 1.7
Chex Quest
Aug 03
- 3,711
- 0
Remember the old Chex Quest game in 1996 by Digital Café as a Chex cereal promotion? I don't, but I remember reading about it. This was an attempt to create a non-violent first person shooter for kids age 6-9 where you can shoot slimy aliens who are trying to take your Chex cereal away.

Team Chex Quest HD have re-created the original game in a modern game engine and its totally free!
https://store.steampowered.com/app/804270/Chex_Quest_HD/
Slay green slime aliens with your special laser weapons and even a spoon. Find the keys and navigate your way through the levels leaving no alien traces behind. There are secret areas, interactive elements and of course a non violent arsenal of cereal weapons.
Proton handled Chex Quest just fine in Steam. I was able to download, launch and play several levels without any bugs or artifacts.
Specs:
Mint 19.3 64-bit
GeForce GTX 1060
Nvidia 440.100
Proton 5.0-9
 ...
...
Team Chex Quest HD have re-created the original game in a modern game engine and its totally free!
https://store.steampowered.com/app/804270/Chex_Quest_HD/
Slay green slime aliens with your special laser weapons and even a spoon. Find the keys and navigate your way through the levels leaving no alien traces behind. There are secret areas, interactive elements and of course a non violent arsenal of cereal weapons.
Proton handled Chex Quest just fine in Steam. I was able to download, launch and play several levels without any bugs or artifacts.
Specs:
Mint 19.3 64-bit
GeForce GTX 1060
Nvidia 440.100
Proton 5.0-9
Terraria Journey's End
Jul 30
- 3,709
- 0
Terraria (GOG) has been a family favorite for a few years now. The four of us will play co-op via LAN for hours each week and eventually get tired of it... then a few months later we'll create a new world and start playing a few hours a week again.
This game is never ending. You can explore, build, craft and fight all kinds of creatures forever. There are costumes, special events, bosses and all kinds of biomes. There is never a dull moment as long as you enjoy digging. You will spend hundreds of hours digging for ores and crafting them into bars to build your weapons, tools, armor and much more.
Terraria has re-invented the platform game with its huge sandbox worlds and non-linear exploration. Go anywhere you want, avoid traps and hordes... store all of your loot and go looking for more. What else could you want?
Quests?
Yes, Terraria has that too...
Tower Defense?
Yes, Terraria has that too...
Trading?
Yes...
This game is never ending. You can explore, build, craft and fight all kinds of creatures forever. There are costumes, special events, bosses and all kinds of biomes. There is never a dull moment as long as you enjoy digging. You will spend hundreds of hours digging for ores and crafting them into bars to build your weapons, tools, armor and much more.
Terraria has re-invented the platform game with its huge sandbox worlds and non-linear exploration. Go anywhere you want, avoid traps and hordes... store all of your loot and go looking for more. What else could you want?
Quests?
Yes, Terraria has that too...
Tower Defense?
Yes, Terraria has that too...
Trading?
Yes...
Assassin's Creed Origins in Proton
Jul 27
- 7,003
- 0
Every Assassin's Creed game I've played has run in Linux with the help of Wine and DXVK. I've always used PlayOnLinux and installed a legacy version of Uplay because of Windows XP compatibility. You can find those step-by-step guides here on GamersOnLinux. There are a LOT of steps and sometimes Uplay will run and other times you have to start over. Once you get the game downloaded you run Uplay offline otherwise a simple update will break it.

Not Any More!!!
Steam and Proton handle downloading Assassin's Creed Origins and running Uplay without issue. Somehow its painlessly compatible with Proton and I was able to run the game first try! That is impressive after all the previous steps I used to run one game.
Thank you Steam!
Assassin's Creed Origin runs great in Mint with my GeForce GTX 1060 and Proton. Frame rates are smooth and traversing around the cities is stunning! I have only taken time to explore...
Not Any More!!!
Steam and Proton handle downloading Assassin's Creed Origins and running Uplay without issue. Somehow its painlessly compatible with Proton and I was able to run the game first try! That is impressive after all the previous steps I used to run one game.
Thank you Steam!
Assassin's Creed Origin runs great in Mint with my GeForce GTX 1060 and Proton. Frame rates are smooth and traversing around the cities is stunning! I have only taken time to explore...
Borderlands 3 in Proton
Jul 24
- 7,844
- 0
Borderlands 3 initially released only on the Epic Store. Later it was released on Steam and of course we wanted to see if Proton could handle it. We prefer a native port like all the other Borderlands, but until then lets play in Proton?

My daughter and I have played through all of the Borderlands games in co-op modes over LAN. They all ran almost flawlessly. In Borderlands 3 they have introduced the ShiFT account which still includes LAN play and online as always. We were not able to play over LAN so I had to purchase two copies of the game. We were able to play in Proton 5 and the game ran decent after the initial stutter of loading shader cache.
As we played there was one serious problem... a video is supposed to play during an early quest with Lilith. The video on the TV never plays and the quest is stuck. After reading several post with Windows and Linux gamers having the same problem, turns out Borderlands is using Media Foundation...
My daughter and I have played through all of the Borderlands games in co-op modes over LAN. They all ran almost flawlessly. In Borderlands 3 they have introduced the ShiFT account which still includes LAN play and online as always. We were not able to play over LAN so I had to purchase two copies of the game. We were able to play in Proton 5 and the game ran decent after the initial stutter of loading shader cache.
As we played there was one serious problem... a video is supposed to play during an early quest with Lilith. The video on the TV never plays and the quest is stuck. After reading several post with Windows and Linux gamers having the same problem, turns out Borderlands is using Media Foundation...
IKAI Demo in PlayOnLinux
Jul 23
- 2,593
- 0
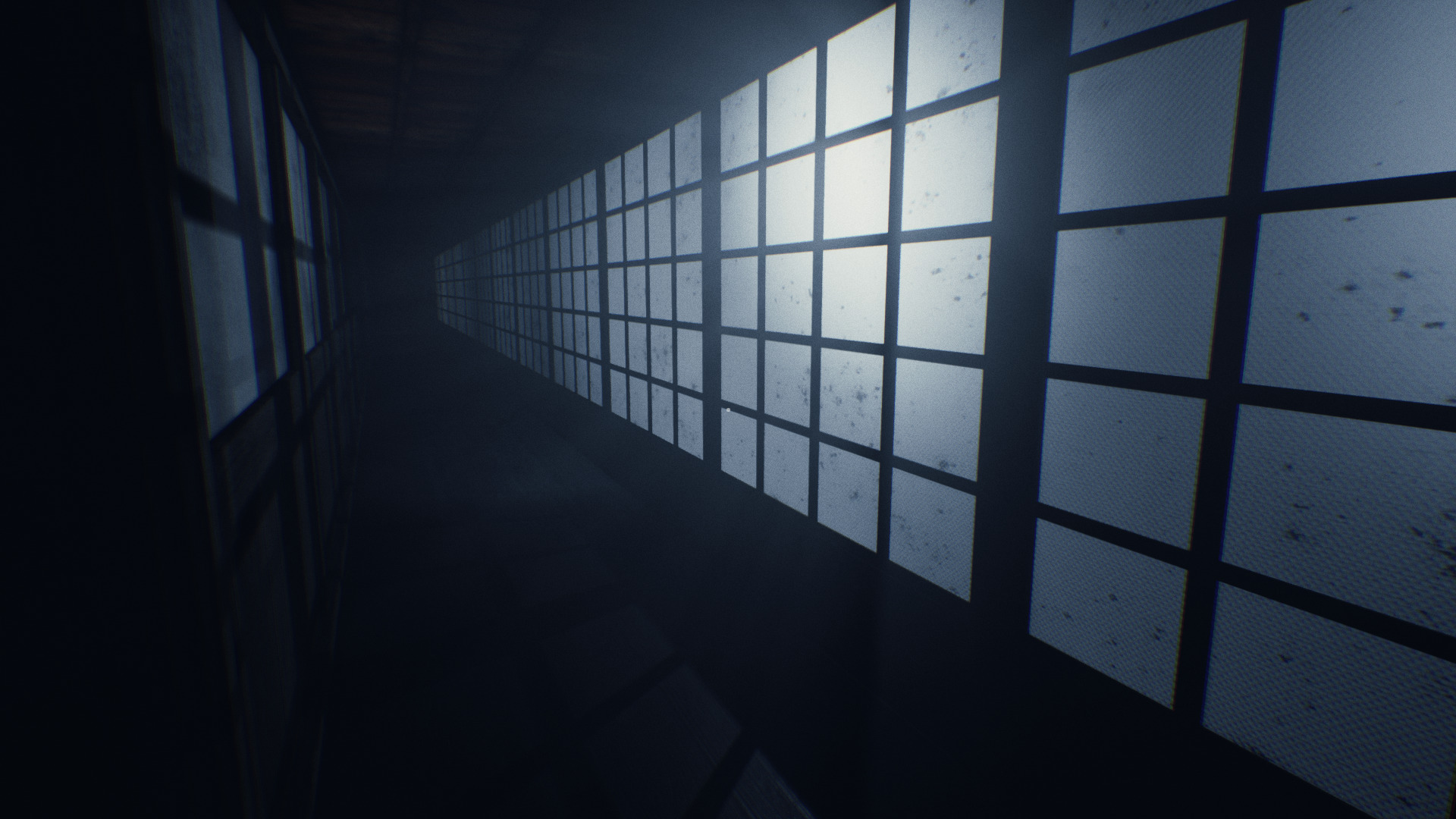
IKAI is a first person horror game in ancient Japan. Play as a priestess and explore a creepy haunted Japanese building looking for a way out. Solve puzzles and don't awaken the evil lurking in the walls.
The visuals and environment are beautifully made in Unreal Engine. The lighting and creepy ambient sounds will force you tread lightly through every room. Inspect objects up close and watch your back.
https://endflame.itch.io/ikai-demo
Specs:
Mint 19.3 64-bit
GeForce GTX 1060
Nvidia 440.59
PlayOnLinux 4.3.4
ProtonGE 5.8 64-bit
DXVK 1.7 64-bit













The visuals and environment are beautifully made in Unreal Engine. The lighting and creepy ambient sounds will force you tread lightly through every room. Inspect objects up close and watch your back.
https://endflame.itch.io/ikai-demo
Specs:
Mint 19.3 64-bit
GeForce GTX 1060
Nvidia 440.59
PlayOnLinux 4.3.4
ProtonGE 5.8 64-bit
DXVK 1.7 64-bit
A Story About My Uncle
Jul 19
- 2,836
- 0
A Story About My Uncle is not a read-along adventure... or a children's book...
This is an epic first person physics adventure where your grappling hook and jump tricks allow you to traverse amazing terrain. Jump super high with your suit and grapple floating islands, rocks and structures. Fling yourself around cliffs and waterfalls above bottomless worlds. Meet alien creatures who inhibit these mysterious floating lands and use energy crystals fly themselves across the landscape. All in the name of finding uncle Fred.
A Story About My Uncle ran great in Steam with my GeForce GTX 1060. I never had any performance issues and the graphics settings were cranked to high. This Linux port made with UDK (Unreal Development Kit) in 2012 by a group of students at Södertörn University.
Specs:
Mint 19.3 64-bit
GeForce GTX 1060
Nvidia 440.100
 ...
...
This is an epic first person physics adventure where your grappling hook and jump tricks allow you to traverse amazing terrain. Jump super high with your suit and grapple floating islands, rocks and structures. Fling yourself around cliffs and waterfalls above bottomless worlds. Meet alien creatures who inhibit these mysterious floating lands and use energy crystals fly themselves across the landscape. All in the name of finding uncle Fred.
A Story About My Uncle ran great in Steam with my GeForce GTX 1060. I never had any performance issues and the graphics settings were cranked to high. This Linux port made with UDK (Unreal Development Kit) in 2012 by a group of students at Södertörn University.
Specs:
Mint 19.3 64-bit
GeForce GTX 1060
Nvidia 440.100
